Learn About Augmented Reality in Retail
Augmented Reality offers significant benefits for your business, such as enhancing your marketing strategy and improving the customer experience....

Phishing emails are deceptive messages sent by cybercriminals to trick recipients into revealing sensitive information, such as passwords, credit card numbers, or social security numbers. These emails often appear to be from a legitimate source, such as a bank, online store, or social media platform, but they are designed to steal personal information.
To understand phishing emails, it's important to be aware of some common techniques cybercriminals use to make their messages seem authentic.
Content of this article
One common technique employed by cybercriminals in phishing emails is spoofing. This deceptive tactic involves manipulating the email to give the appearance that it originates from a trusted source by utilizing a fabricated email address or tampering with the sender's name. In addition, these cybercriminals may incorporate logos, graphics, or other elements to create the illusion that the email is genuinely from a legitimate company.
Here are some common examples used in phishing emails:
Spoofing: Phishing emails frequently spoof the sender's address to make it seem like they are from a reputable source, such as your bank, credit card company, or even a friend or colleague. These emails may also use logos and other branding elements from these organizations to make them seem more credible.
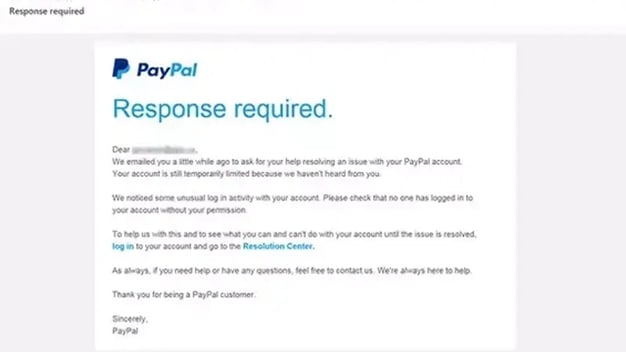 An example of a phishing email sent with the PayPal brand.
An example of a phishing email sent with the PayPal brand.
Urgency: Phishing emails often create a sense of urgency to pressure you into clicking a link or opening an attachment without thinking. They may use phrases like “urgent action required,” “your account is at risk,” or “limited time offer.”
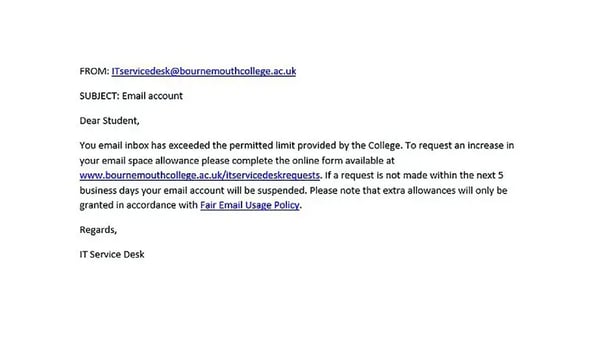 Urgency Email Example
Urgency Email Example
Personalization: Phishing emails can be made to look more convincing by making them personalized. They may include your name, address, or other personal information that the fraudsters have obtained from other sources.
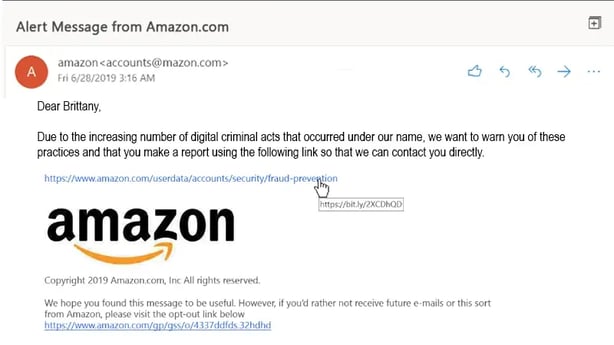 Personalization Email Example
Personalization Email Example
Phishing is the most common way for cybercriminals to launch attacks, and your entire workforce must know how to identify phishing emails. In today's globe, everyone is at risk of being targeted, and email security is the first line of defense.
Phishing attacks are becoming increasingly sophisticated, and it is unrealistic to expect IT and security teams to recognize all of them and fight them alone with technology. The truth is that since humans are the targets, they must be the primary defense against attackers attempting to infiltrate information systems.
Given the spell check feature available on most email clients and the autocorrect or highlight features in web browsers, one would anticipate emails originating from a professional source to be devoid of any grammatical or spelling errors.
An effective method to detect a potential phishing attack is to carefully examine email addresses, links, and domain names for inconsistencies. It is advisable to cross-reference the originating email addresses with previous correspondence. When encountering an email with an embedded link, it is recommended to hover the pointer over the link to observe the displayed destination. If an email claims to be from PayPal but the domain of the link does not include "paypal.com," it is a clear indication of a fraudulent email.
Note: It's crucial not to click on links if the domain names do not match.
If an email requests an unusual action that deviates from standard procedures, it should be regarded as a potential indicator of a malicious message. For instance, if an email claims to be from the IT department asking you to install a program or click on a link to patch your PC, yet these tasks are typically handled centrally, you have likely received a phishing email. It is crucial not to follow the instructions in such cases.
One of the most sophisticated forms of phishing emails occurs when an attacker creates a deceptive landing page that recipients are directed to through a link in an email that appears official. This fraudulent landing page typically includes a login box or requests a payment to resolve an alleged issue. If the email was unexpected, recipients should navigate to the supposed website by manually entering the URL instead of clicking on any links.
This precaution ensures that login credentials are not entered into a fake site and prevents any payments from being made to the attacker.
If you receive an email with an attached file from an unfamiliar source or if you were not expecting to receive a file from the sender, it is necessary to exercise caution when opening the attachment. If the attached file has an extension commonly associated with malware downloads (such as .zip, .exe, .scr, etc.) or has an unknown extension, it is recommended to scan the file for viruses before opening it.
Phishing attacks pose a significant threat to businesses of all sizes, exposing them to severe repercussions such as data breaches, financial losses, and damage to their reputation.
Safeguarding your company necessitates adopting a comprehensive strategy that tackles technical and human vulnerabilities. Consider implementing the following essential measures:
By implementing these measures, you can greatly diminish the likelihood of your company becoming a target of phishing attacks. It is important to bear in mind that security is an ongoing endeavor, necessitating a continuous review and updating of your defenses to stay ahead of ever-evolving threats.
Related content

Augmented Reality offers significant benefits for your business, such as enhancing your marketing strategy and improving the customer experience....

With the continued shift to digital banking and the rise of fintech are we seeing the inevitable demise of traditional brick and mortar FIs? Not...

Are you seeking to enhance the scalability and efficiency of your customer response system? Artificial intelligence in chatbots can be an excellent...